sigma
Google Cloud Platform: Authorization
Service accounts are the standard authorization mechanism in Google Cloud Platform. While they are mainly for server-to-server interaction, Sigma uses them for authorizing itself to access your cloud resources during development time as well.
Authorizing Sigma for your GCP project
This can be under one of two scenarios:
You are new to Sigma (or have just created an account)
Please refer Grant GCP access to Sigma section under our GCP getting-started guide.
You have already authorized Sigma with an AWS key pair
In this case you would not be seeing the Cloud Credentials page upon log-in, as described above.
Authorizing via the GCP Resources pane
This is a temporary authorization; the service account key will be stored in your browser’s session storage and will be automatically cleared when you log out or close the browser tab.
-
Switch to the editor mode.
-
Switch to the GCP Resources child tab on the Resources tab of the left pane.
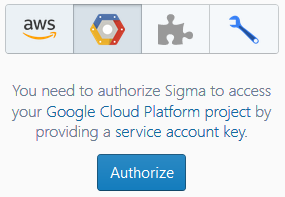
-
Click Authorize.
-
Paste the service account key file content into the input field of the GCP Service Account Key dialog, and click Save.
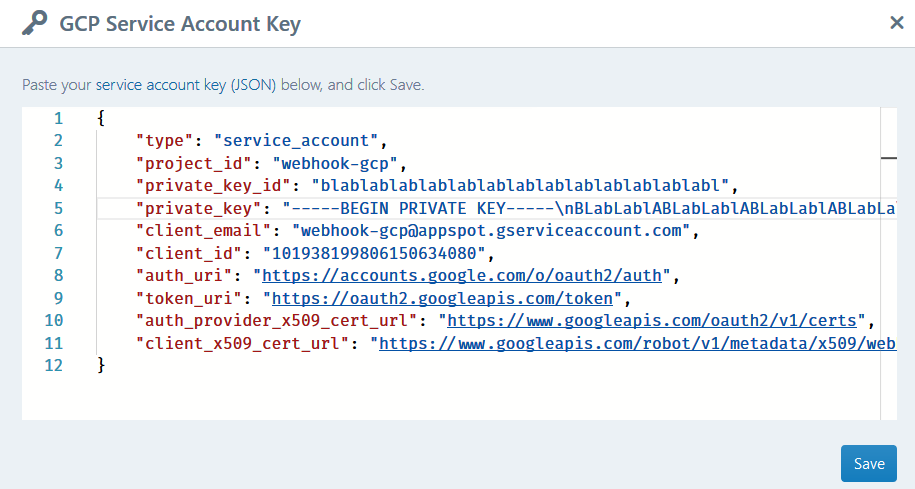
-
If the service account key is accepted, the GCP Resources tab will start displaying available GCP services, along with the authorized GCP project name at the bottom.
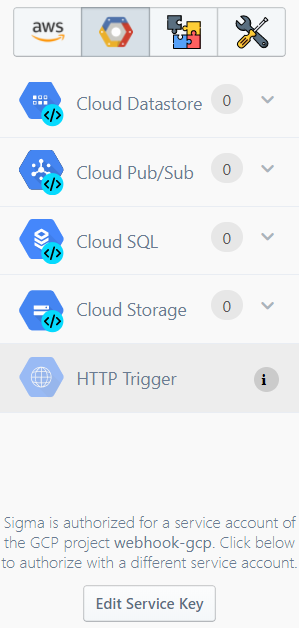
Authorizing via the Settings page
This approach provides an option to persist your credentials into Sigma’s Amazon Cognito secure storage; so you can make a permanent authorization.
-
Open the user menu on the top right corner, and choose Settings.
-
On the Settings page, select Cloud Credentials tab on the left.
-
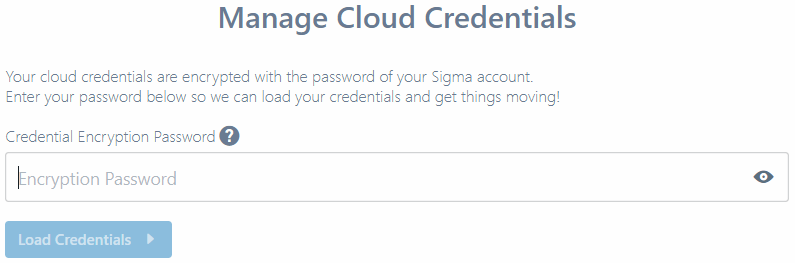
If you have already saved credentials for other platforms, Sigma will prompt you for an encryption password/PIN so that it can load and decrypt them. Provide the password/PIN, based on how you logged in - using a username or via social media.
-
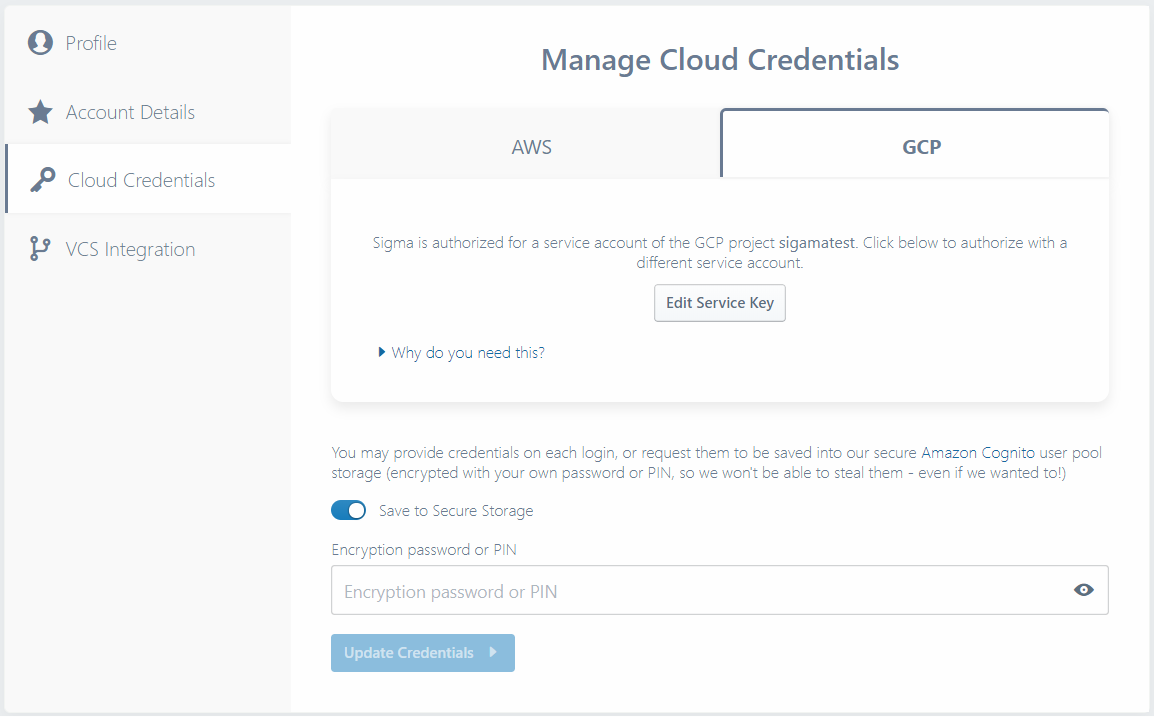
Now follow the instructions as described under Grant GCP access to Sigma section of the getting-started guide to provide GCP (and optionally AWS) credentials, and choose to persist (or not persist) them.
-
When done, click Update Credentials on the bottom.
Sigma will validate the provided credentials, persist them if required, and display a confirmation if all goes well.
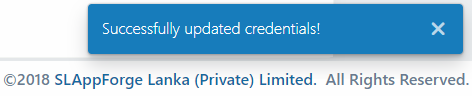
If there are any issues, an appropriate error message will be displayed against the Update Credentials button, including the name of the cloud platform where the failure occurred; in this case, revise the corresponding credentials and try again.
After authorization
Once authorization is done via any of the above means, the GCP resources pane will start displaying a list of natively supported GCP services. You can drag them into your code as operations (and triggers, depending on whether you are in a GCP-based project) similar to other platforms like AWS.
Since the service account usually has full permission to all resources in your GCP project,
you can use any Google Cloud API in your project - even if they are not present in Sigma’s supported GCP resource list.
Simply write your custom API invocation logic based on the googleapis client,
and they should work fine at runtime.
You can commit, build and deploy your solution, configure cloud function settings or set environment variables similar to how they are done on an AWS-based project.
How Sigma uses your service account key
Within the IDE
Sigma uses the key to obtain an OAuth2 access token
in order to access Google Cloud APIs on your behalf (within the scope https://www.googleapis.com/auth/cloud-platform).
This is used to obtain details of existing cloud resources in your GCP project during drag-n-drop operations,
and to invoke Cloud Storage, Cloud Build
and Deployment Manager API operations on your behalf.
For GCP deployments
Google Cloud Functions use implicit authorization via Application Default Credentials. Hence your service account key is not included into the deployment configurations.
For other platform (e.g. AWS) deployments
Sigma includes your service account key as an environment variable,
and uses it to create an authorizer and feed it to the
googleapis client library at runtime.
Hence it is advisable to use a customized service account with only the necessary permissions,
when integrating with GCP on a non-GCP runtime.